Overcoming the challenges of cybersecurity awareness
Аuthor: Goce Stevanoski, MSc
Has a master’s degree in information science – computer engineering, C3I member,
working in cybersecurity, computer networks, telecommunication, and system administration.
The range of threats in the Internet space is enormous and does not tend to decrease. New technologies, with their diversity in the structure, contribute to the continuous emergence of new vulnerabilities, and thus new threats to privacy, confidential data, and availability of services.
In such circumstances, all information technology users should regularly improve their understanding and attitude towards the safe use of these information technologies. Besides the technical measures for securing the data, which is processed in the IT infrastructure, the training of all personnel in understanding the threats that can arise from working with IT devices, is a necessity.
Large-scale technical measures contribute to the protection of our data, these measures are accurate, timely, comprehensive, and respond very well when are well managed. But the human factor is not excluded from the impact on these technical measures. Human virtues and flaws play a major role in the implementation of effective cybersecurity. It is the flaws that can contribute to the occurrence of vulnerabilities even in a perfectly designed technical system, intended to protect the information in cyberspace. The saying “The chain is as strong as its weakest link” best reflects the need for continuous improvement of cyber awareness.
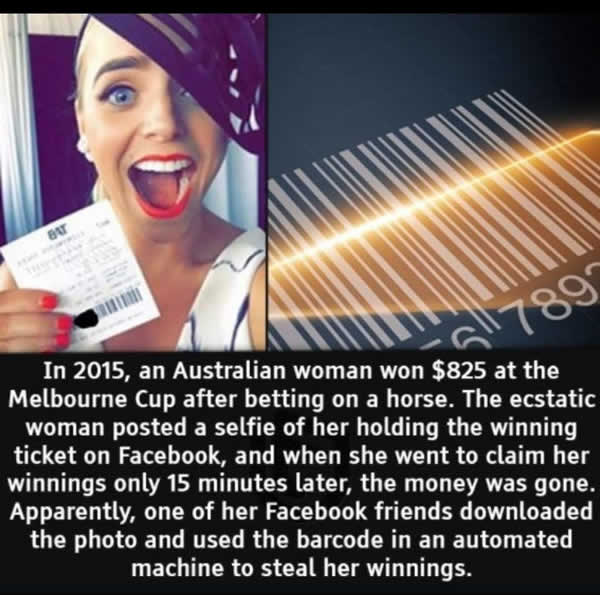
When working with IT devices, people’s reaction is fast and reckless, almost as a conditioned reflex of the content they see. As a result, malicious emails are unknowingly opened, malicious links are clicked on web pages, and content that would otherwise remain private is shared. This behavior makes them vulnerable to cyber threats. The tendency to change people’s habits cannot be done overnight. This process must take planning and implementation of different measures and activities. The result should be increased awareness of the threats in cyberspace. Depending on the needs and conditions for implementation, the measures and activities that can result in increased cyber awareness can be taken in the short and long term.
The transition to an information society, with full digitalization, means preparing the institutions, businesses, and citizens for life and work within that society. The educational process is one of the pillars of that transformation. Good educational programs can help in preparation for the successful functioning of the digitally connected world. Besides others, these programs should include training on protection from threats in cyberspace. The educational process in the early school-age of children, through practical examples, can point to the threats that lurk on the Internet, such as misrepresentation, data theft, installation of malicious programs, misinformation, etc. Older children must be trained in recognizing and dealing with cyberbullying, financial fraud, cyber predators, sextortion, publishing content that will cause them problems in the future, etc.
Certainly, successful cooperation at the institutional level in a country would seriously affect the development of cyber awareness. The cooperation must include specific activities between the state bodies (ministries, agencies), local level bodies, educational institutions, as well as the non-governmental and private sector, to ensure the best possible continuous training of the citizens. In that direction, and with the accomplishment of various workshops, exercises, seminars, and conferences, we can increase awareness of threats in cyberspace and improve cooperation at the institutional level to deal with those threats. This approach reduces the gap between the institutions, enables the establishment of networks of contacts, improves the exchange of information, and strengthens the mutual trust of the staff. In that way, a stronger (integrated) institutional infrastructure is formed that knows how to recognize a threat in cyberspace and take measures to eliminate it.
Considering that over 82% of people in the Republic of North Macedonia are users of some of the social networks, it is clear that they are most vulnerable to threats in cyberspace through these platforms. Social networks are advertised as friendly and fun networks that are providing an easy and simple way to communicate, exchange pictures/videos and news. Such openness and easy access contribute to unprepared joining to social networks from many people. In such a case, without prior knowledge of the platforms, private and confidential information is easily shared, which, if they end up in the wrong hands, can easily be misused. Additionally, these users also become vulnerable to disinformation campaigns, often for political purposes. Therefore, just as social networks allow easy connections to their platforms, they should also have a simple interface for training new users in the consequences of using the social network. They should enable fast and intuitive management of the information that is posted/shared on the network platform.
Media campaigns are a great way to stay focused on the problems that arise in cyberspace. Whether aimed at children, young people, or the adult generation, media campaigns can help maintain attention and continuity in dealing with cyber threats. In this way, directly, through campaigns that show measures to eliminate threats in cyberspace, and subtly, through constant reporting of perceived problems, awareness of the risks in cyberspace can be maintained.
There is no doubt that the development of the information society will renew the old ones, but will also bring new, more modern threats in cyberspace. Dealing with those threats is a complex problem that should involve different entities and of course their aspects. Awareness of the threats in cyberspace must become part of our daily lives, we must live with it, notice the threats, and take measures to manage them.
This article is supported by the Metamorphosis Foundation and Techsoup. The views expressed in this publication are those of the author and do not always reflect the views of the Metamorphosis Foundation, Techsoup and C3I.[:]